Computer Spam Virus

Common Computer Viruses Malware How To Detect And Remove Them

Spyware Computer Virus Spam Malware Icons Stock Vector C Popicon

Full Email Inbox Of Spam Spammer Letters In Mailbox On Computer Screen Computers Virus Scam Messages In Letterbox Stock Vector Illustration Of Cartoon Office

Spam Virus In Restrict Sign On Laptop Computer On Sun Ray Background Vector Illustration Cybercrime Concept Design Stock Illustration Download Image Now Istock

How To Remove A Virus Or Malware From Your Pc Kaspersky

Top 10 Symptoms Of A Computer Virus
The most common form of spam is email spam, but the term also applies to any message sent electronically that is unsolicited and bulk This includes instant message spam, search engine spam, blog spam, Usenet newsgroup spam, wiki spam, classified ads spam, Internet forum spam, social media spam, junk fax spam, and so on.
Computer spam virus. Email spam Also known as unsolicited or unwanted email, email spam mostly spreads malware via links in the message that lead to phishing websites or other sites hosting malware Virus hoax email messages These emails contain a false warning about a nonexistent threat and are considered to be a form of socially engineered email virus or worm These messages could also instruct the recipient to take some action, which also includes forwarding the warning to all their contacts. The concept that spam and virus email could actually choke the Internet, rendering it virtually useless, is no longer a paranoid fantasy it's a possible reality If the trend continues without new solutions found, the gains made by the availability of broadband will be negated by the time spent filtering junk. To avoid your computer from getting a virus, follow these suggestions Do not open an email attachment unless you know whom it's from and whether or not you were expecting it Delete emails immediately if you do not know the person who sent you the email Upload antivirus software on your computer.
Virus hoax A virus hoax is a false warning about a computer virus Typically, the warning arrives in an email note or is distributed through a note in a company's internal network These notes. Conficker which is also known as Downup, Downadup, and Kido is a type of computer virus that usually targets Microsoft Windows Operating system The virus was first identified in November 08 This virus uses flaws of Windows operating system to fetch the administrator password via dictionary attacks while forming a botnet. Protecting Computer from Virus No matter whether your computer is virus infected or not, there are some basic steps that you need to take to protect your device and files Install a trusted antivirus program to guard your computer There is a lot of antivirus software both for free and for cost.
The malware payload may enslave your computer into a botnet for the purposes of sending out more spam More often than not the payload will be a Trojan As we noted in our Cybercrime Tactics and Techniques Report , the majority of malware attacks in 18 for both businesses and consumers were identified as Trojans of some kind. Computer viruses are named after human viruses that spread from person to person A computer virus is a program made of malicious code that can propagate itself from device to device Like a cold that alters your wellbeing, when your computer is infected, it alters the way your computer operates, can destroy your files, or prevent it from. Generally, spam won’t harm a computer, unless the recipient receives so much spam that it fills up their email quota Spam can also contain a link to a website or attachment containing a virus that could cause harm Recipients should always be wary of attachments and links in emails, especially emails that look like spam.
If you gave a scammer remote access to your computer, update your computer’s security software Then run a scan and delete anything it identifies as a problem If you gave your user name and password to a tech support scammer, change your password right away. TrojanDroppers are complex programs used by cyber criminals to install malware Most antivirus programs do not detect droppers as malicious, and hence it is used to install viruses Ransomware It is a type of Trojan (Trojan ransom) that can encrypt the data on your computer/device. A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself Like other types of malware, a virus is deployed by.
Install antivirus software from a reputable vendor Update it and use it regularly In addition to scanning for viruses on a regular basis, install an "on access" scanner (included in most antivirus Use a virus scan before you open any new programs or files that may contain executable code. Most commonly viruses are spread unknowingly from one infected computer to another via emails and instant messaging Often, they are disguised as images, cards, and media files They can also come from software or other programs downloaded from the Internet. Use the Runbox spam filter and virus filter Maintain your trainable spam filter by always correcting it when it Always check the sender and recipient information of suspicious messages Spam will typically be sent from falsified Be careful in setting up autoreplies, as they may verify the.
According to the same Nucleus Research report, businesses lose more than $70 billion annually because of computer viruses — and the cost continues to rise as every major company moves to a fully digital workplaceEvery time you download a computer virus or click on a spam email by accident, you are wasting money, endangering your. According to the same Nucleus Research report, businesses lose more than $70 billion annually because of computer viruses — and the cost continues to rise as every major company moves to a fully digital workplaceEvery time you download a computer virus or click on a spam email by accident, you are wasting money, endangering your. The most common form of spam is email spam, but the term also applies to any message sent electronically that is unsolicited and bulk This includes instant message spam, search engine spam, blog spam, Usenet newsgroup spam, wiki spam, classified ads spam, Internet forum spam, social media spam, junk fax spam, and so on.
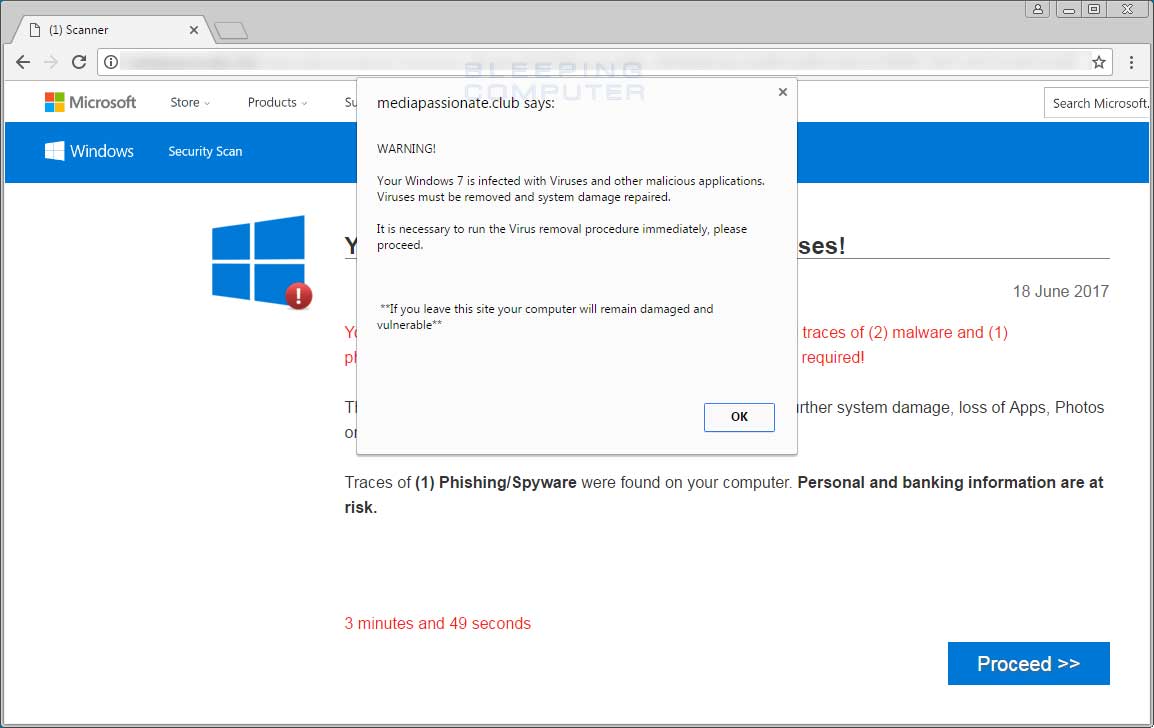
The Virus Alert from Microsoft tech support scam is a browser based scam that tries to trick people into thinking that Microsoft has detected that they are is infected and blocked their computer. Emails infected with a virus usually appear like any normal email in your inbox. Spam can be used to spread computer viruses, trojan horses or other malicious software The objective may be identity theft , or worse (eg, advance fee fraud ) Some spam attempts to capitalize on human greed, while some attempts to take advantage of the victims' inexperience with computer technology to trick them (eg, phishing ).
When a computer virus infects your computer, it may slow it down and stops it working properly There are three main ways that your computer may have become infected with a computer virus The first way your computer could become infected from removable media, like a USB stick If you insert a USB stick or disk into your computer from an unknown source, it may contain a virus Sometimes hackers leave infected USB sticks or disks in people’s workplaces, or public places like cafes to spread. A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code If this replication succeeds, the affected areas are then said to be "infected" with a computer virus Computer viruses cause billions of dollars' worth of economic damage each year. Professional anti spam and threats server protection for ISP, SME, SMI & large companies It offers the best protection against viruses, malware, phishing and other threats and eliminates up to 99% of spam Learn more about MailCleaner.
If you clicked an ad in a popup on a free streaming site, you may want to scan your computer for viruses and malware We put together a guide on how to remove malware Windows If you're on a Windows computer, follow these instructions to remove any malware that may be causing the popup to appear Mac. If you gave a scammer remote access to your computer, update your computer’s security software Then run a scan and delete anything it identifies as a problem If you gave your user name and password to a tech support scammer, change your password right away. Spam and email messages loaded with malware are still considered to be one of the most effective means of social engineering employed by hackers to spread and infect users with viruses and also to attack the networks of their victims' companies Types of Email Viruses.
Press CTRL, ALT, DEL keys together to open the Microsoft Windows Task Manager Click on the “Processes” tab, look for something dubious that is the adware which causes intrusive “Microsoft detected malicious virus” scam then rightclick it and select “End Task” or “End Process” option. A computer virus is a malicious piece of computer code designed to spread from device to device A subset of malware, these selfcopying threats are usually designed to damage a device or steal data Think of a biological virus – the kind that makes you sick. A file infector can overwrite a computer's operating system or even reformat its drive The macro virus takes advantage of programs that support macros Macro viruses usually arrive as Word or Excel documents attached to a spam email, or as a zipped attachment Fake file names tempt the recipients to open the files, activating the viruses.
The zombie machines are generally personal computers owned by unsuspecting private citizens who happened to contract the SoBig virus The virus opens their machine up to spammers, who can then route spam emails through their machines. Spam and viruses Spam is increasingly generated from computers by viruses Virusmakers and spammers are combining their efforts to compromise innocent computer users’ systems and converting them into spamsending “drones” or “zombies”. Most of the viruses that spread on your computer are delivered through attachments These attachments are sent via email most often from people you know who are unaware of the virus or through spam mail that wants to advertise a message to you So, what happens once you receive an email infected with a virus?.
To unblock your computer, enter security key or call for help (Toll Free) A The “Microsoft has detected a malicious virus alert and blocked your computer” popup alert a misleading webpage that is created in order to trick you and other unsuspecting users into believing that the computer has been blocked by Microsoft. Spam is unsolicited Internet content that is typically sent in bulk for advertising purposes from an unknown sender Spam is sometimes defined more broadly as any unsolicited emailHowever, the advancement of email filtering and privacy laws have led spammers toward other mediums for sending messages, specifically social media. As features and functionality in computer world gets updated, the scams in malware also increasingly released to market by the intruders The motive behind the prevalence of computer virus scams is to trick the users by supplying fake antivirus software and cause them a critical system failure or you may get a phone call claiming that they are from technical support company to offer free service.
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code If this replication succeeds, the affected areas are then said to be "infected" with a computer virus Computer viruses cause billions of dollars' worth of economic damage each year. EFax Email Virus removal guide What is eFax Email Virus?. Top MostDestructive Computer Viruses Ever The virus was programmed to spam people with multiple emails that clog an inbox in short order Netsky Virus Netsky Virus Well, this virus spread itself through emails and Windows networks The Netsky virus spoofs email addresses and propagates through a 22,016byte file attachment.
A computer virus is a program made of malicious code that can propagate itself from device to device Like a cold that alters your wellbeing, when your computer is infected, it alters the way your computer operates, can destroy your files, or prevent it from working altogether Get the Free Pen Testing Active Directory Environments EBook. Last Words on Top Types of Computer Viruses – Names of Computer Viruses – 18 Updated These viruses are very dangerous and can harm instantly your PC/Laptops I have shared all the types of computer viruses You can check the virus description and later remove that from your PC/computer. The most common form of spam is email spam, but the term also applies to any message sent electronically that is unsolicited and bulk This includes instant message spam, search engine spam, blog spam, Usenet newsgroup spam, wiki spam, classified ads spam, Internet forum spam, social media spam, junk fax spam, and so on.
Virusmakers and spammers are combining their efforts to compromise innocent computer users’ systems and converting them into spamsending “drones” or “zombies” These malicious programs spread rapidly and generate massive amounts of spam pretending to be sent from legitimate addresses. Hitman Pro is a second opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc) that have infected your computer despite all the security measures you have taken (such as anti virus software, firewalls, etc). A computer virus, much like a flu virus, is designed to spread from host to host and has the ability to replicate itself Similarly, in the same way that flu viruses cannot reproduce without a host cell, computer viruses cannot reproduce and spread without programming such as a file or document.
Remove Fake popup or tech support scam messages that warn the computer is infected Some fraudulent companies use fake popup warnings that claim your computer is infected with a virus These Popups are made to look like a Norton virus scan alert or other types of legitimate security warning To identify and avoid fake tech support scams. A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself Like other types of malware, a virus is deployed by. The reason why Trojans, like the Recorded You Masturbating EMail Spam Virus Trojan are a significant threat, is that it has multiple different malicious functions that are utilised on your computer The features of a Trojan may vary, depending on what type it is, but it is safe to assume that the Recorded You Masturbating EMail Spam Virus.
How to Scan Your Computer for Viruses By default, Windows 10 is always scanning your PC for malware with the integrated Windows Security application, also known as Windows Defender You can, however, perform manual scans On Windows 10, open your Start menu, type “Security,” and click the “Windows Security” shortcut to open it. Spam is the electronic equivalent of the ‘junk mail’ that arrives on your doormat or in your postbox However, spam is more than just annoying It can be dangerous – especially if it’s part of a phishing scam Spam emails are sent out in mass quantities by spammers and cybercriminals that are looking to do one or more of the following. Well, add me to the Gotcha List I was a victim of a computer virus scam Here's how it happened and how you can avoid being a victim, which is especially timely since it's National Cybersecurity.
The virus is a malicious program that enters into the computer without your permission and can affect your data and operating system Well, viruses are of different types as there are trojan horses and much more However, have you ever thought about creating a virus?. Overview Spam is probably the single most annoying artifact of the Internet's success If you have email, you've probably received spam Both the amount of spam and the number of complaints about it have increased to such a level that, were it not to take action, many of Stanford's core email services would no longer be usable Antispam options Stanford offers three main. Email Virus In general, a computer virus or worm is a selfreplicating program capable of being spread by emails or by inserting copies of itself into other documents or programs Viruses that spread via email are capable of knocking out systems burdened by the huge amounts of generated emails, thus causing severe headaches for individual users.
The virus opens their machine up to spammers, who can then route spam emails through their machines Since the IP addresses of these machines are new, they do not appear in the IP address blacklists and millions of spam emails can route through them before they get blacklisted. "eFax Email Virus" is a spam campaign used to proliferate a trojantype virus called HancitorIt is virtually identical to many other spam campaigns, such as Important Documents IRS, Sage Invoice, and Payslip SPAM The deceptive "eFax Email Virus" email contains a message stating that users have received a fax message. This type of email spam will include an attachment or a link to a file that will trigger some virus of malware to install to the recipients computer when the attachment is opened or the link visited Sometimes they are sent automatically from one computer to others using scripts in the virus that cause the recipient computer to forward it on to other people in their address book without the recipient’s knowledge.

K2 S Filtering The World Spam Virus And Malware Protection

What Are Computer Viruses Actually Vpnoverview

How To Spot A Computer Virus In An Email Inbox 6 Steps

Computer Virus Wikipedia

Email Spam Virus Filtering Integra Network Services
Email Spam Virus Icon Download On Iconfinder

How Computer Viruses Work Howstuffworks

Is Your Incident Response Plan Ready For Novel Computer Viruses Global Privacy Security Blog
Malware Online Scam Spam Computer Virus Icon Vector Image

Anti Virus Anti Spam Solutions Pinnacle Computer Services

8 Different Types Of Malware United States Cybersecurity Magazine

What Are The Common Types Of Computer Viruses What To Watch Out For And What They Do Canton Computers The Ultimate Computer Store

What Is An Email Virus And How Can Healthcare Businesses Can Protect Themselves Paubox

How To Remove A Computer Virus Youtube
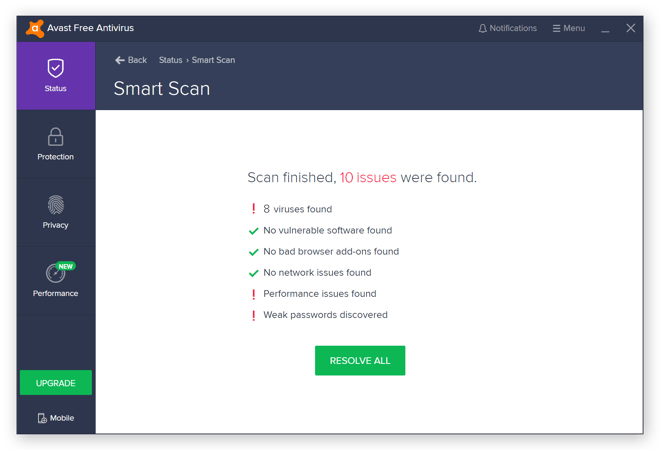
What Is A Computer Virus Pc Virus Definition Avast

Viruses Worms Trojans And Spam
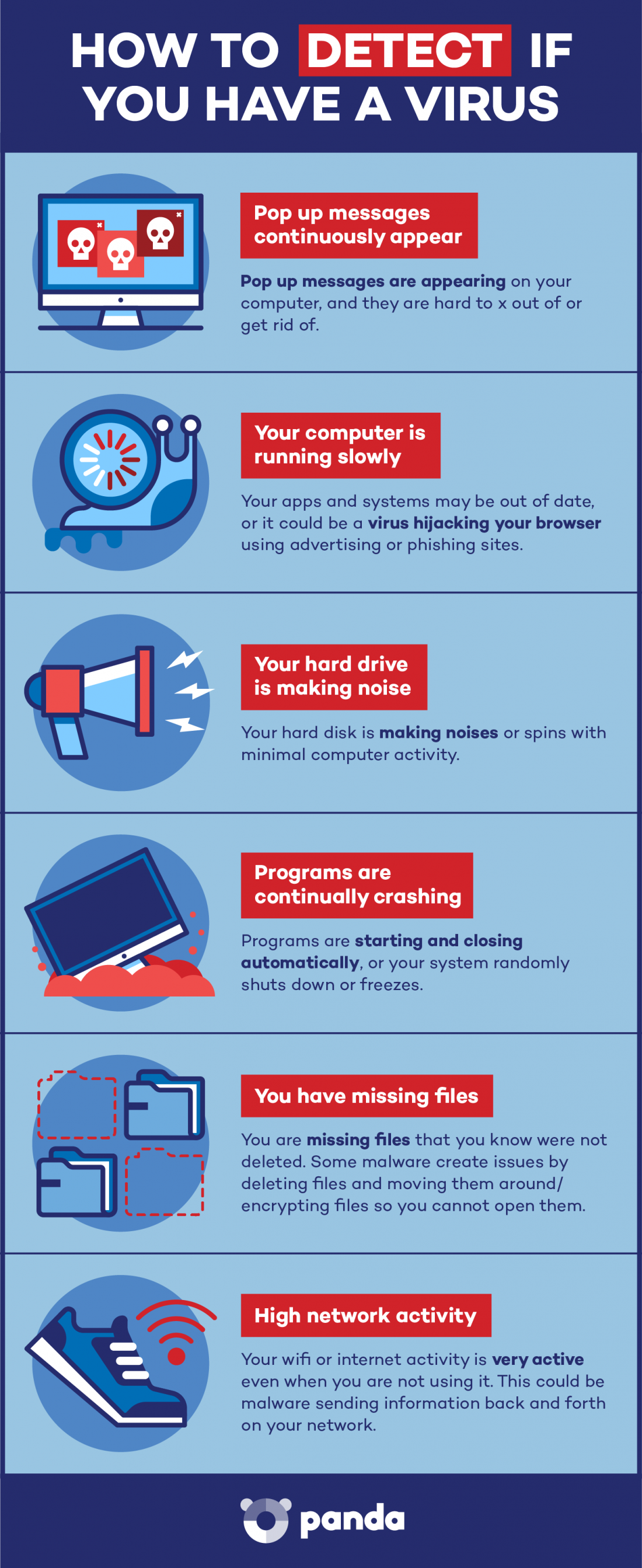
How To Get Rid Of A Virus Panda Security
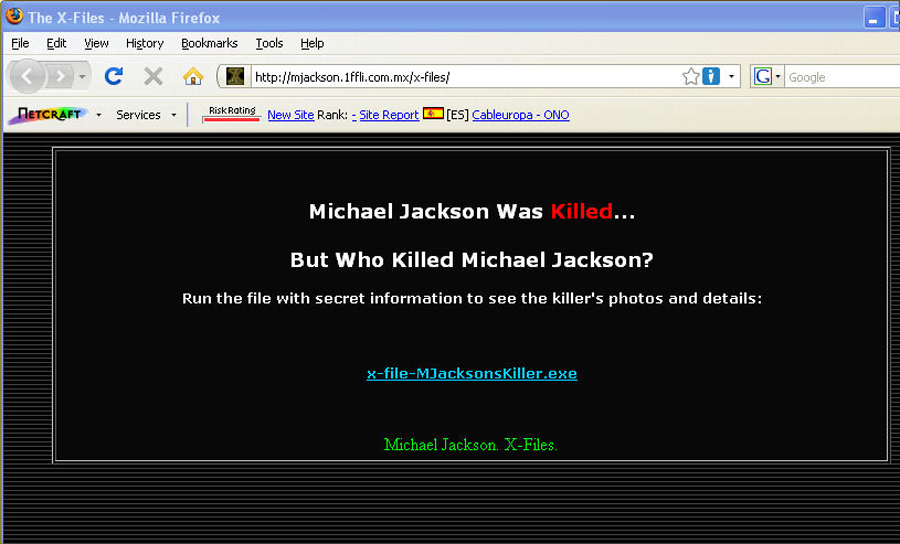
Michael Jackson Finally Gets His Own Computer Virus Science 2 0
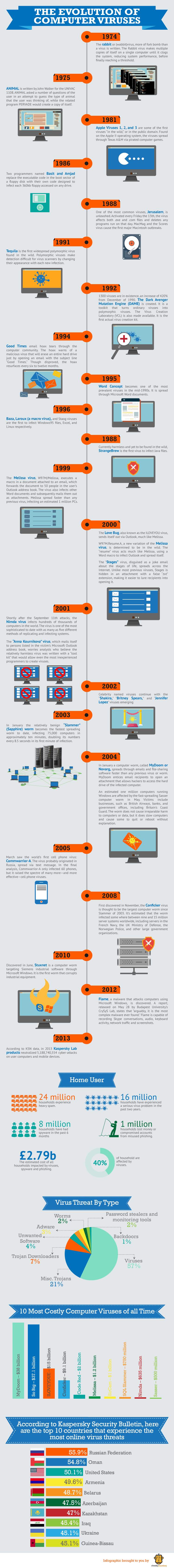
The Evolution Of Computer Viruses Cheeky Munkey

How To Protect Against Computer Viruses rp

Remove Virus Spam

Zombie Computing Wikipedia

Why Didn T Your Anti Virus Software Stop Spam And Infections

No Spam Email With Skull And Cross Bones Computer Virus In Restrict Sign Isolated On White Background Vector Illustration Prohibited Circle Design Stock Illustration Download Image Now Istock
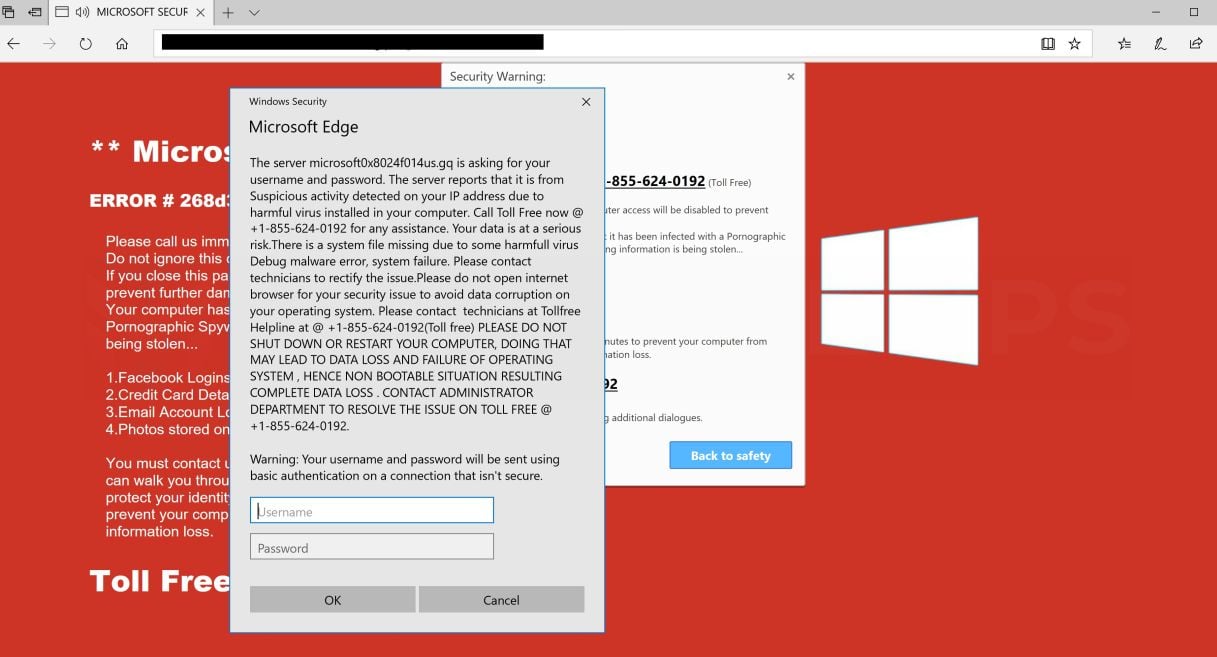
Remove Attention Your Computer Has Been Infected Pop Up Scam Alerts
Laptop Computer Spam Virus Spam Image Icon Vector Illustration Royalty Free Cliparts Vectors And Stock Illustration Image
Premium Vector Computer Bug Email With Virus Mobile Spam Malware And Cyber Attack Icons
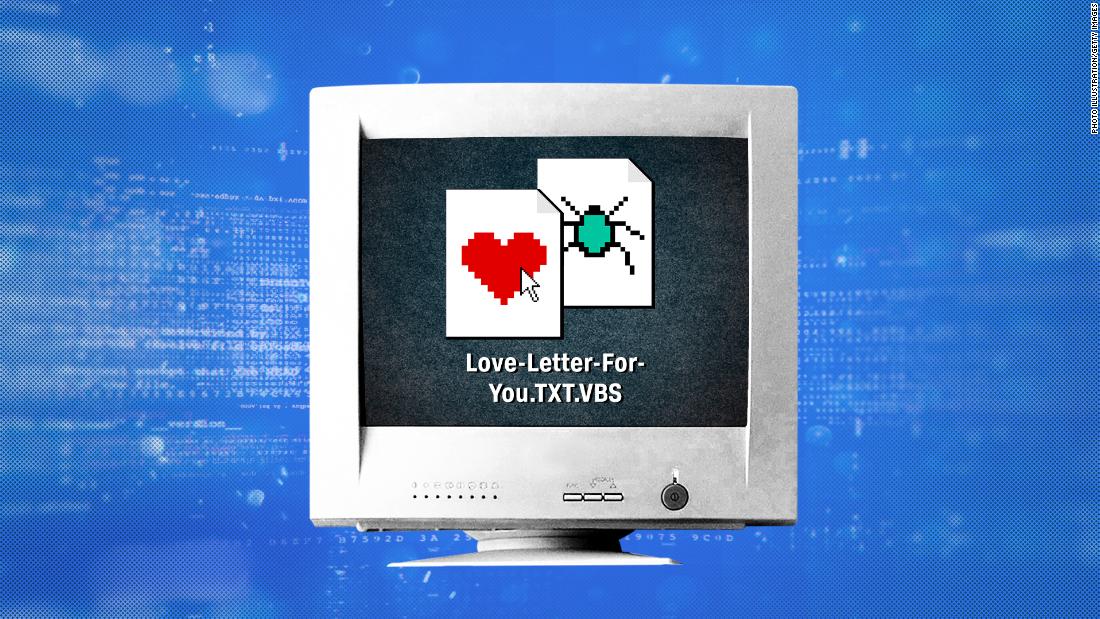
I Love You How A Badly Coded Computer Virus Caused Billions In Damage And Exposed Problems Which Remain Years On Cnn
Spam Virus Computer Laptop Internet Security Concept Stock Photo Picture And Royalty Free Image Image

Problems Due To Malware Viruses Spam And Other Malicious Actions Problems Due To Malware Viruses Spam And Other Malicious Actions

How To Spot A Computer Virus In An Email Inbox 6 Steps

Computer Virus And Spam Removal Miami Ft Lauderdale Home And Business
Email Malware Spam Virus Icon Download On Iconfinder
Computer Viruses And Spam Vector Concept With Icons Of Hacker S Royalty Free Cliparts Vectors And Stock Illustration Image

Scareware Alert Your Computer Is Not Infected Pc Ninja

How To Get Rid Of A Computer Virus Norton
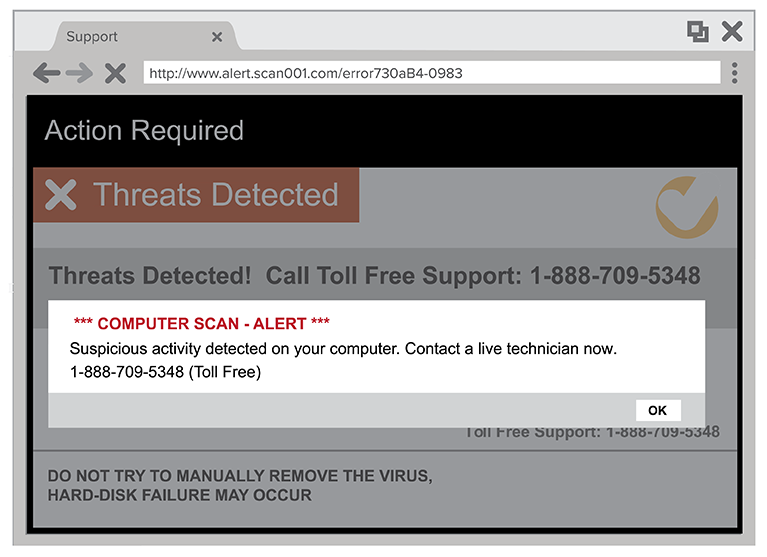
How To Spot Avoid And Report Tech Support Scams Ftc Consumer Information

Amazon Com Online Safety Scams Spam Viruses And Clouds Cyber Security Community Book 1 Ebook Perry A M Kindle Store

5 Of The Worst Computer Viruses Ever Youtube
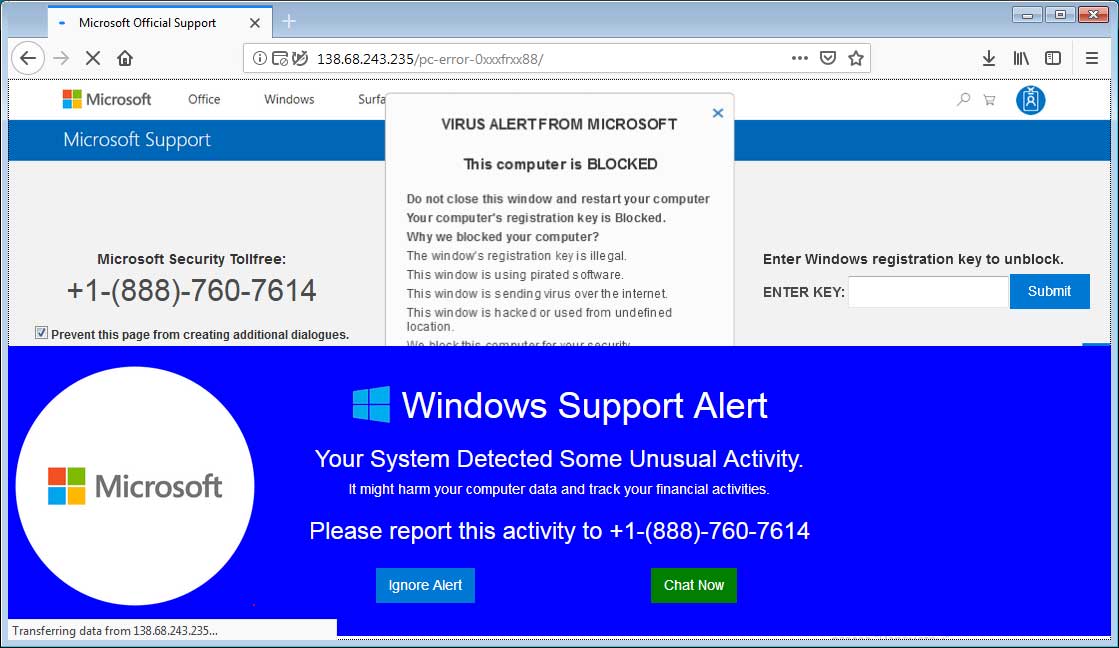
Remove The Virus Alert From Microsoft Tech Support Scam

Spam Virus Computer Monitor Internet Security Concept Stock Photo Alamy
Types Of Computer Viruses Tutorialsmate

How To Remove Your Computer Was Locked Pop Ups Microsoft Scam

Computer Viruses

Premium Vector Computer Technology Danger Spam Virus Cyber Security
:max_bytes(150000):strip_icc()/CHROMEBOOKVIRUS-70f436f7387c42c3a52a2c2483f84458-748280ff925c4edeb4bb343d5e52a78a.jpg)
Can Chromebooks Get Viruses
Remove The Your Windows Is Infected Popup Scam

What Is A Computer Virus Types Of Computer Viruses Updated

3 Ways To Get Rid Of Viruses Spyware And Malware

Virus Free Computer Learn About Encryption Software Anti Virus Programs Spam Security Spyware Malware Removal Cyber Security And More Pc Security Tips To Keep You Safe From Dangerous Computer Threats By Ben K
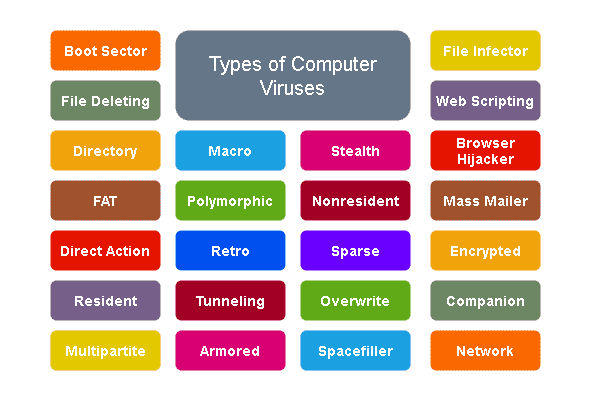
Types Of Computer Viruses Tutorialsmate
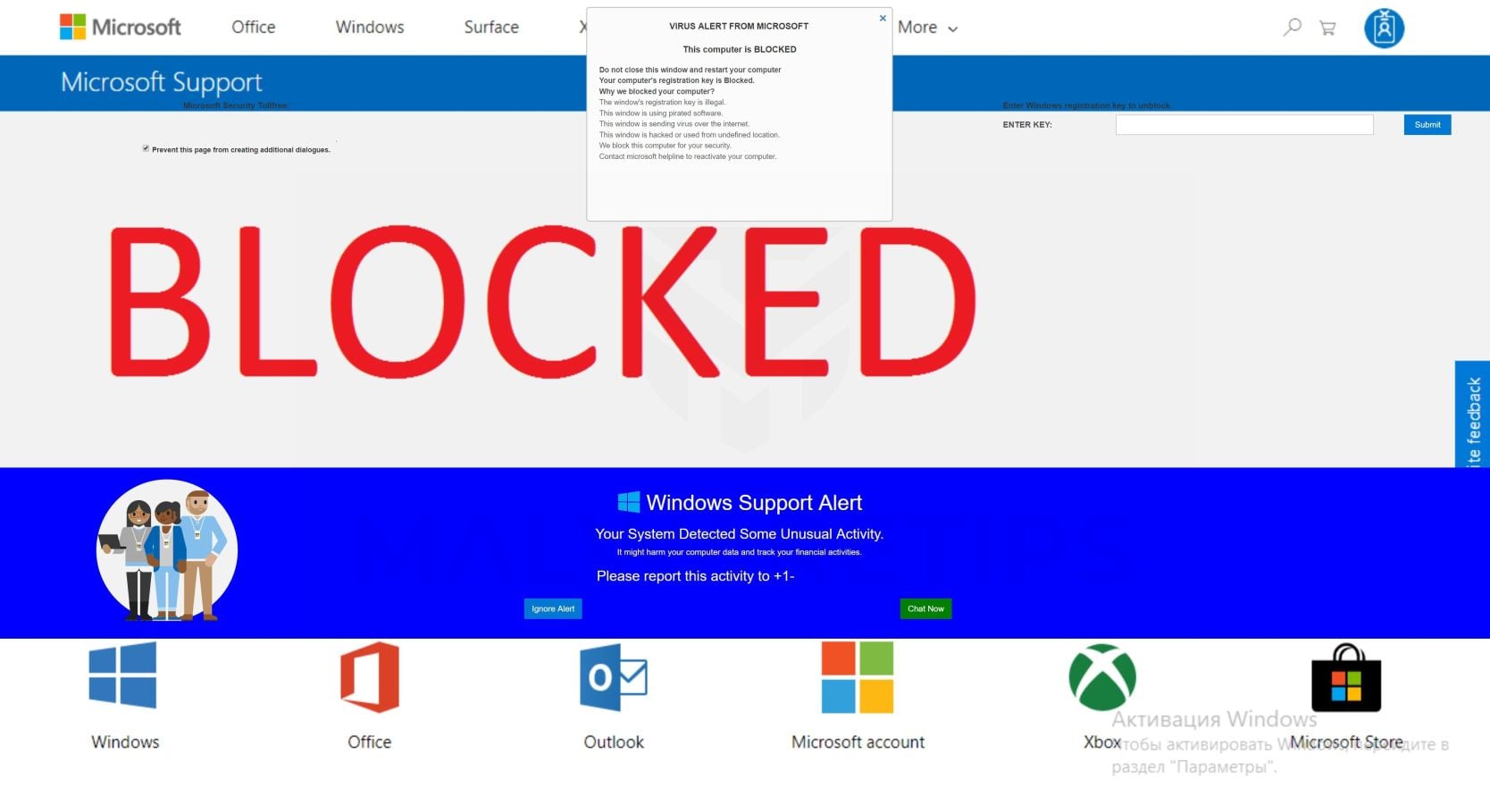
How To Remove Virus Alert From Microsoft Pop Up Scam
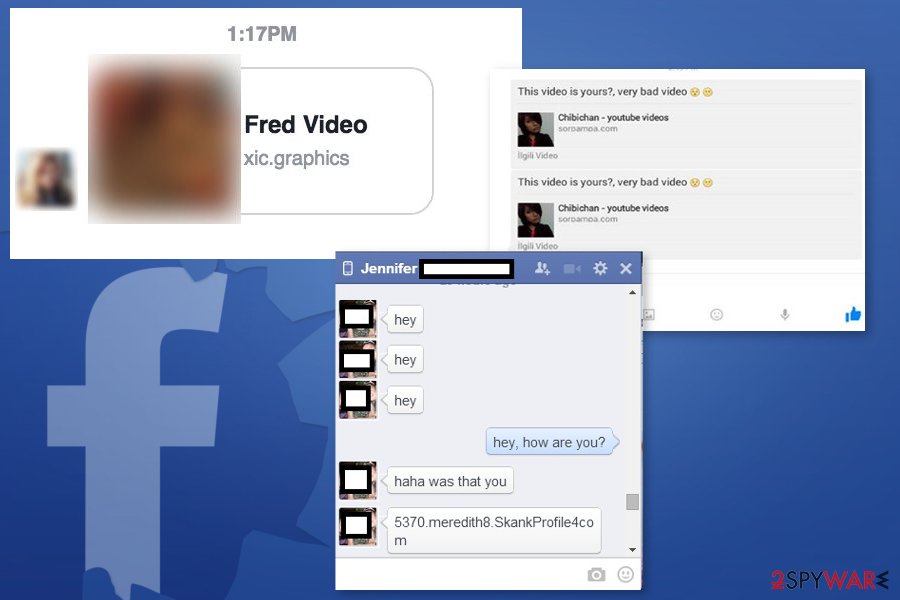
Messenger Virus 21 Update A New Threat For Facebook Users

Want To Avoid A Computer Virus Follow These 5 Steps

Computer Virus Infographics Visual Ly
Email Virus Top 3 Ways An Email Virus Infects Computers

How Spyware Works Howstuffworks
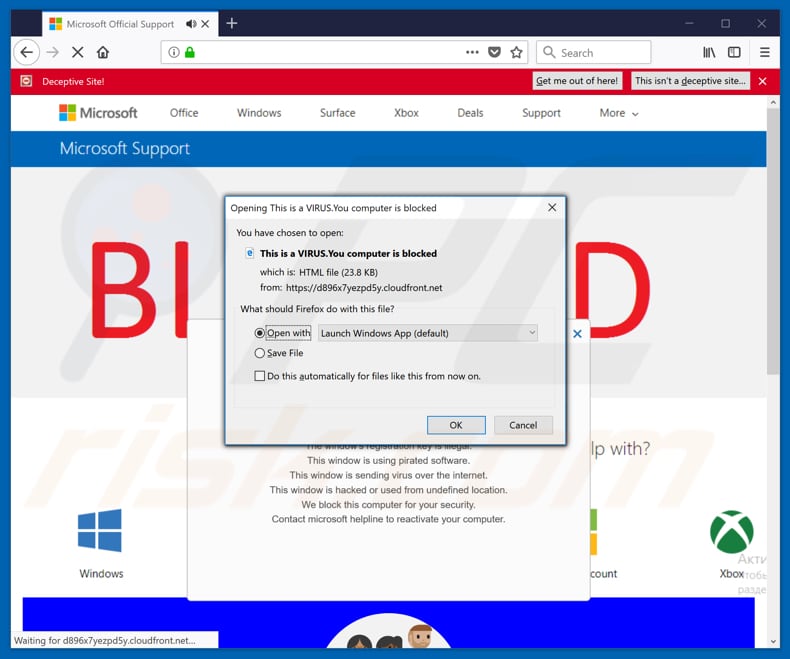
How To Remove This Is A Virus You Computer Is Blocked File Scam Virus Removal Guide Updated

Does An Antivirus Program Prevent Spam
/https://public-media.si-cdn.com/filer/top-10-computer-viruses-631.jpg)
Top Ten Most Destructive Computer Viruses Science Smithsonian Magazine

How To Tell If Your Computer Has A Virus And What To Do About It

Computer Laptop Virus Fraud Or Spam Notification Internet Online Virus Alert Icon Canstock

Spam Email Effective Methods To Protect Your Email

10 Free Virus Removal And Malware Removal Tools Comparitech
How To Remove A Mac Computer Virus Malware Spyware Maintenance And Cleaning 19 Youtube

10 Most Dangerous Computer Viruses Education Today News

Easy Ways To Avoid Computer Viruses Tech Talk Outsource It

What Is A Computer Virus Virus Protection Removal Malwarebytes

Premium Vector No Spam Spam Email Warning Concept Of Virus Piracy Hacking And Security Envelope With Spam
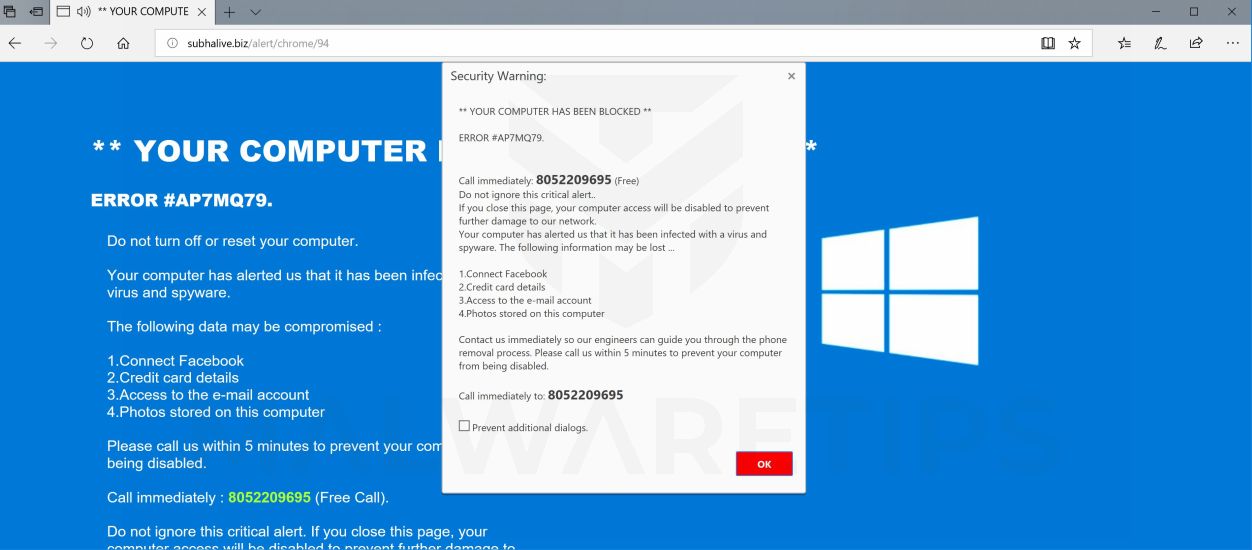
Remove Your Computer Has Been Blocked Pop Up Scam

Viruses And Spyware Get Safe Online

How To Scan Remove And Protect Your Chromebook From Viruses Complete Guide Platypus Platypus

Email Spam Wikipedia

Scammers Use Old Browser Trick To Create Fake Virus Download Malwarebytes Labs Malwarebytes Labs
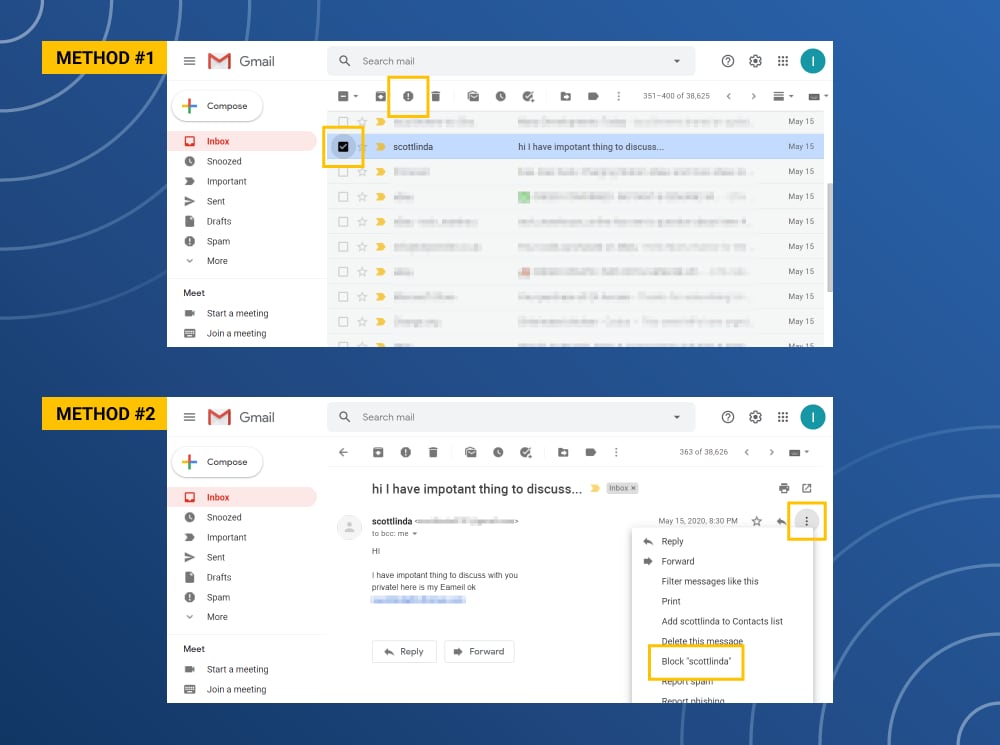
5 Simple Ways To Get Rid Of Spam Emails Nortonlifelock

Common Types Of Malware Today And How To Deal With The Risks Correctly
Noroc Broadband Llc Harrisburg Broadband Internet Service Provider Isp Spam Filtering Computer Forensics Data Recovery
Malware Spam Online Scam Computer Virus Icon Vector Image

Hacker 2x2 Flat Design Concept With Spam Phishing Ddos Attack Royalty Free Cliparts Vectors And Stock Illustration Image

How To Stop E Mail Spam Spyware Malware Computer Viruses And Hackers From Ruining Your Computer Or Network The Complete Guide For Your Home And Work Bruce C Brown Amazon Com Books
Malware Difference Between Computer Viruses Worms And Trojans Youtube

How To Spot Avoid And Report Tech Support Scams Ftc Consumer Information

Computer Hacker Cyber Phishing Virus Infographic Stock Vector Royalty Free

5 Simple Ways You Can Fight Spam And Protect Yourself
Bug Mail Malware Spam Virus Icon Download On Iconfinder

Computer Viruses 8 Ways To Avoid Them
Laptop Computer Spam Virus Spam Image Icon Vector Illustration Material Red Color Stock Illustration Download Image Now Istock

What Is Malware Everything You Need To Know About Viruses Trojans And Malicious Software Zdnet

Computer Virus Malware Spam And Hacker Attack Vector Image
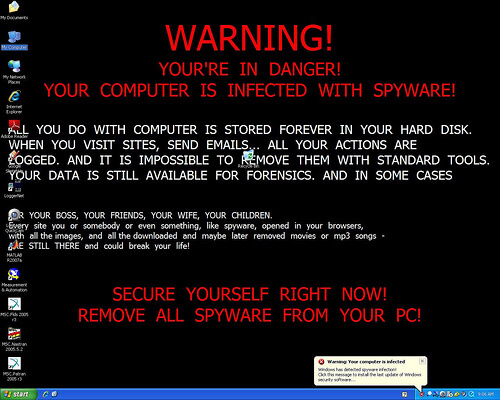
Viruses Network Security Scapegoats Aruba Blogs

Computer Virus Vs Worm What S The Difference Avast

Scareware Alert Your Computer Is Not Infected Pc Ninja
What Is The Need Of Anti Spam Protection Quora
How To Remove I Contaminated Your Machine With A Virus Email Scam Virus Removal Guide Updated



